The DORA (Digital Operational Resilience Act) is a set of regulations created by the European Union to improve the digital security and resilience of the financial sector. It consists of multiple parts, including regulations and technical standards. The regulations lay out the core requirements for financial institutions and critical third-party service providers, while the technical standards provide more specific details on how to implement these requirements.
The DORA package is quite complex and includes a large volume of documents. This can be challenging for financial institutions to navigate and ensure compliance. Keeping pace with the DORA has emerged as a critical challenge for compliance and regulatory professionals across the European Union. As financial entities strive to maintain operational resilience, the sheer volume of regulatory publications demands a strategic approach to ensure comprehensive and timely compliance.
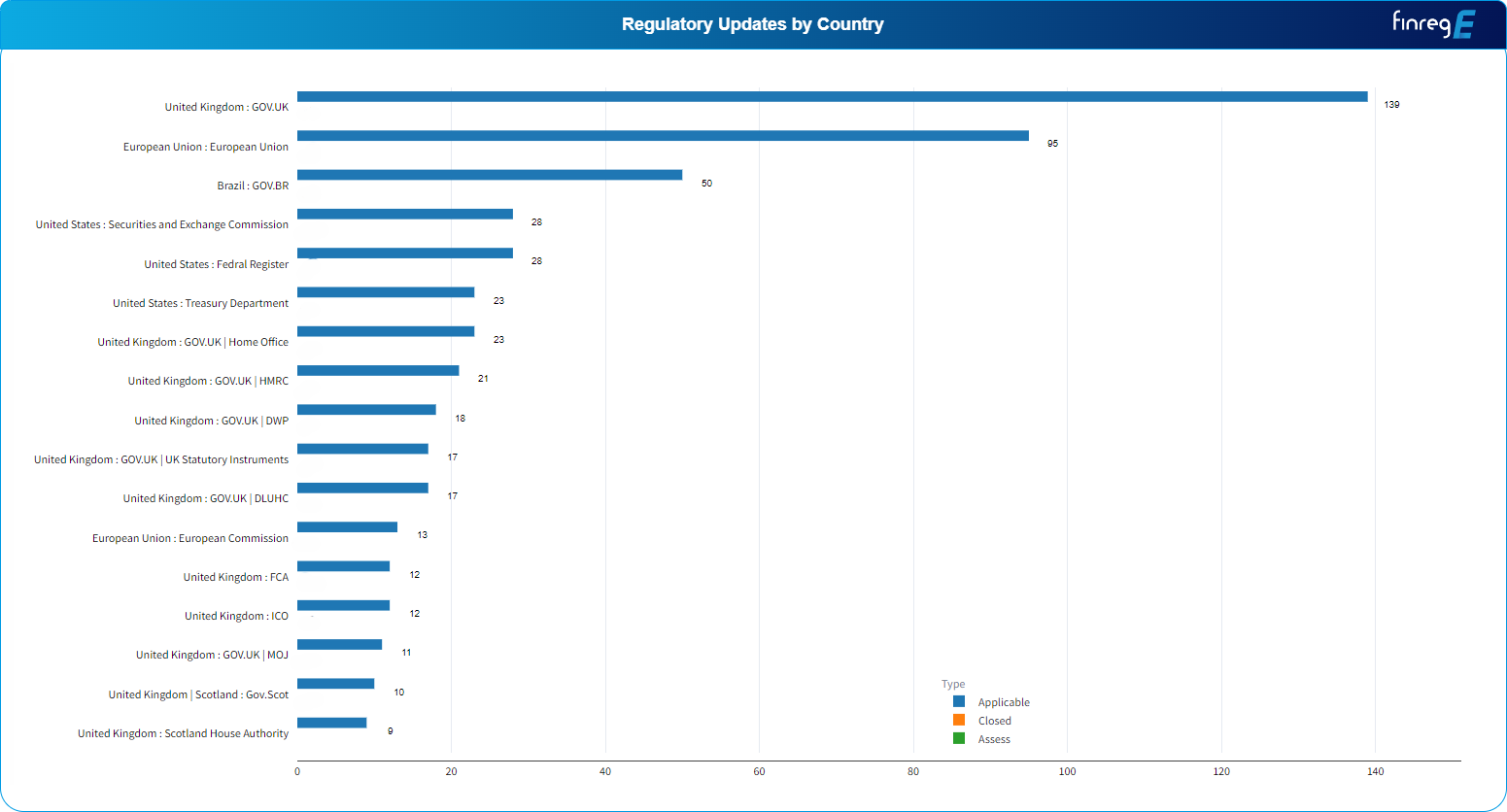
Since September 2021, the European regulatory bodies have issued a staggering 290 publications related to DORA, underscoring the urgency and complexity of this far-reaching legislation. Manually navigating through this avalanche of information is a daunting task, requiring financial institutions to divert valuable resources and expertise towards deciphering the intricate requirements set forth by the European Supervisory Authorities and local jurisdictional supervisors.
The Core DORA EU Package
The core DORA package consists of the following key regulation:
- Regulation on digital operational resilience for the financial sector: This foundational regulation lays out the framework aimed at enhancing the digital operational resilience of the financial sector. It mandates financial entities to have robust Information and Communication Technology (ICT) systems and tools in place, ensuring they are secure, resilient, and capable of withstanding cyber threats and other digital disruptions.
- Directive on the digital operational resilience for the financial sector: The directive complements the regulation by requiring EU member states to adapt their national laws to ensure a harmonized approach across the EU for digital operational resilience. It focuses on oversight, governance, and the integration of digital resilience measures into the broader regulatory framework for financial entities.
- Delegated Regulation determining the amount of the oversight fees to be charged by the Lead Overseer to critical ICT third-party service providers and the way in which those fees are paid : This delegated regulation outlines the financial aspects of regulation, specifically detailing how the oversight fees are determined and collected from critical ICT third-party service providers. It covers the calculation methods for fees, payment procedures, and the responsibilities of the Lead Overseer in managing these processes.
- Delegated Regulation specifying the criteria for the designation of ICT third-party service providers as critical for financial entities: This regulation sets forth the criteria used to identify which ICT third-party service providers are considered critical for the financial sector. It ensures that those providing essential services to financial entities are subject to appropriate oversight and compliance standards, safeguarding the sector’s operational resilience.
- Regulatory Technical Standards (RTS) on ICT risk management framework and on simplified ICT risk management framework: These standards provide detailed guidelines on how financial entities should manage ICT risks. They include requirements for establishing an effective ICT risk management framework and a simplified version for smaller entities, ensuring all financial institutions can maintain their digital operational resilience.
- RTS on criteria for the classification of ICT-related incidents: This document specifies how financial entities should classify ICT-related incidents based on their severity, impact, and other relevant factors. It aims to standardize the approach to incident reporting and ensure timely and effective responses to potential threats.
- RTS to specify the policy on ICT services supporting critical or important functions provided by ICT third-party service providers (TPPs): These standards define the policies for ICT services that support critical or important functions provided by third-party providers. They focus on ensuring that these services meet high resilience standards, minimizing risks to the financial sector.
- Implementing Technical Standards (ITS) to establish the templates for the register of information: This document outlines the technical specifications for the templates used by financial entities to register information as required under DORA. It standardizes the format and content of the information to be registered, facilitating consistency and accessibility across the sector.
How FinregE’s Global Horizon Scanning Solution Keeps You Abreast of DORA in Real-Time
FinregE’s Horizon Scanning solution acts as an indispensable ally for financial institutions to navigate the web of regulatory publications on DORA institutions needed to keep on top of. FinregE provides an unrivalled real-time ability to capture every development at the European level and by local supervisors, providing regulatory and compliance team with a comprehensive view of DORA’s evolution, from its inception to its eventual adoption and commentary by local jurisdictional supervisors.
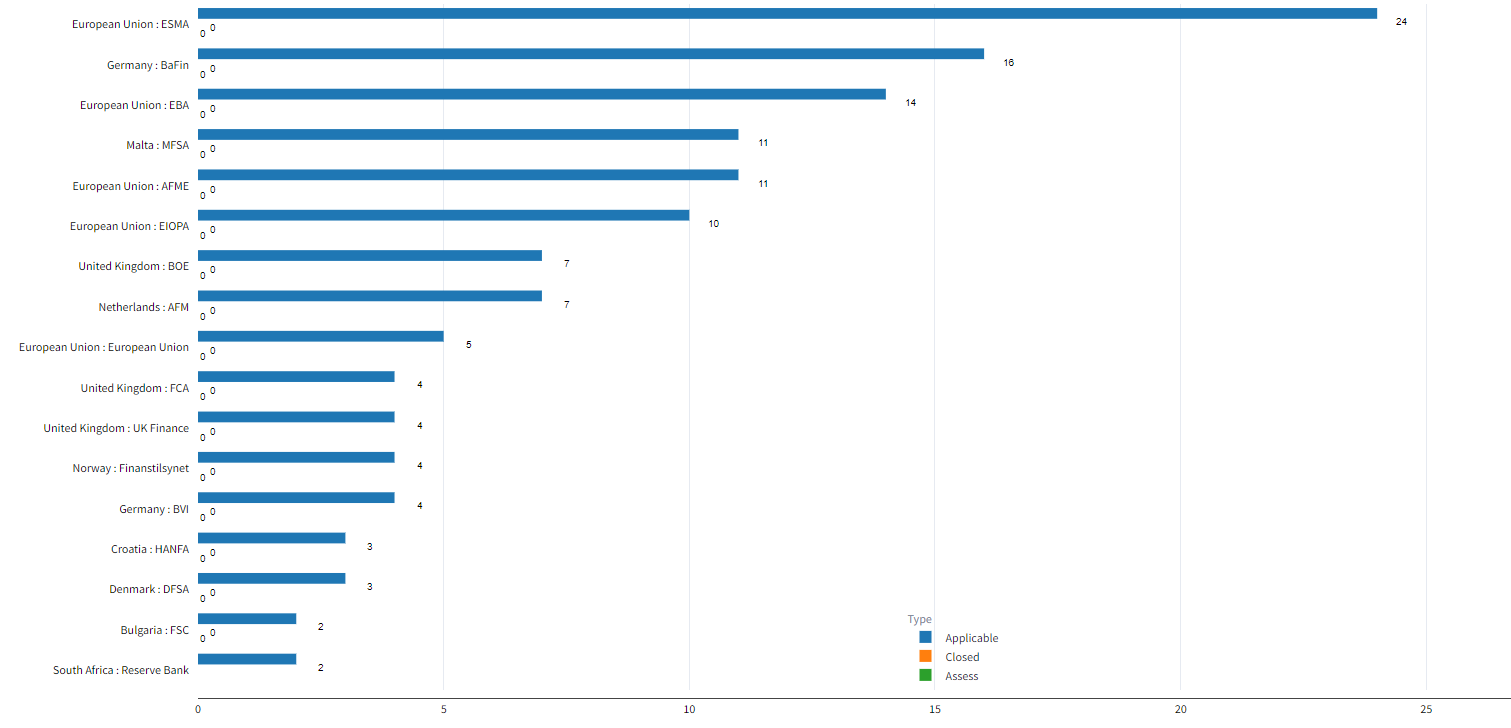
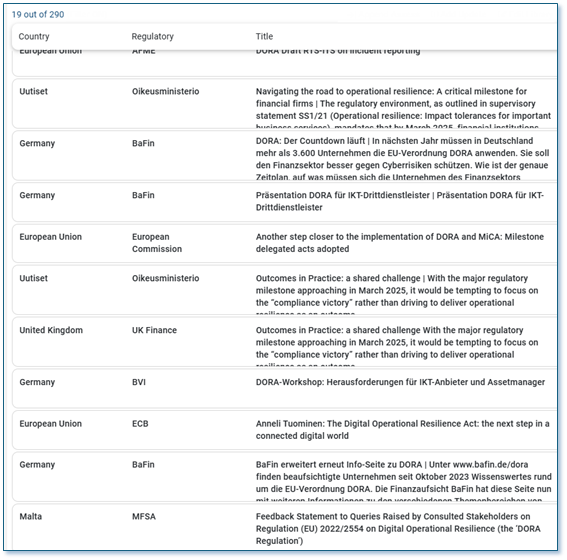
In addition to this, FinregE’s integrated workflows provide effortless dissemination of every relevant publication as it is released, thus enabling compliance teams to swiftly integrate the regulatory updates into their regulatory change implementation plans, allowing to take a proactive approach to DORA compliance.
In response to this regulatory challenge, FinregE’s horizon scanning solution is tailored to the needs of the financial services industry. Our state-of-the-art technology harnesses the power of automation to comprehensively scan, monitor, and analyze every relevant DORA publication, ensuring that no critical update goes unnoticed.
FinregE’s automated reporting and impact assessment workflows also assist in streamlining the process of communicating and addressing regulatory developments across the organization. Compliance teams benefit from a centralized platform that facilitates timely dissemination and analysis, ensuring a cohesive and coordinated response to DORA’s evolving requirements.
How FinregE’s AI RIG Saves Time to Condense and Interpret DORA
The true value of FinregE’s Horizon Scanning solution extends far beyond mere monitoring and dissemination of regulatory publications. FinregE’s AI-powered Regulatory Insights Generator (RIG), a cutting-edge Language Model trained on regulatory and legal texts, the solution offers an unprecedented level of efficiency and insight.
Historically, compliance teams would have dedicated three to four months to meticulously manually interpret and understand the intricate requirements outlined across the regulations and technical standards of DORA. RIG condenses this work into a matter of minutes, with its advanced natural language processing capabilities.
FinregE’s RIG harnesses the power of artificial intelligence to comprehensively analyze and interpret the entire corpus of DORA regulations, extracting and synthesizing key requirements, obligations, and compliance criteria.
With a simple query, compliance professionals can leverage RIG's vast knowledge base to gain a comprehensive understanding of DORA's mandates, eliminating the need for time-consuming manual research and interpretation.
This groundbreaking solution not only accelerates the interpretation process but also ensures a consistent and accurate understanding of regulatory expectations. RIG’s ability to distill complex legal and regulatory language into concise and actionable insights empowers financial institutions to respond swiftly and confidently to DORA’s evolving landscape.
By seamlessly integrating RIG into FinregE’s Horizon Scanning solution, clients can streamline their entire DORA compliance workflow, from monitoring regulatory updates to interpreting requirements and developing tailored implementation plans. This holistic approach condenses a process that once spanned months into a matter of weeks, enabling financial institutions to reallocate valuable resources and focus on strategic initiatives that drive operational resilience.
FinregE’s AI-driven RIG represents a paradigm shift in the way financial institutions approach regulatory compliance, ushering in a new era of efficiency, accuracy, and agility in navigating the complexities of the Digital Operational Resilience Act and beyond.
Example Results from user queries on DORA regulation and technical standards using RIG.
DORA REGULATION
Question | FinregE’s RIG Response |
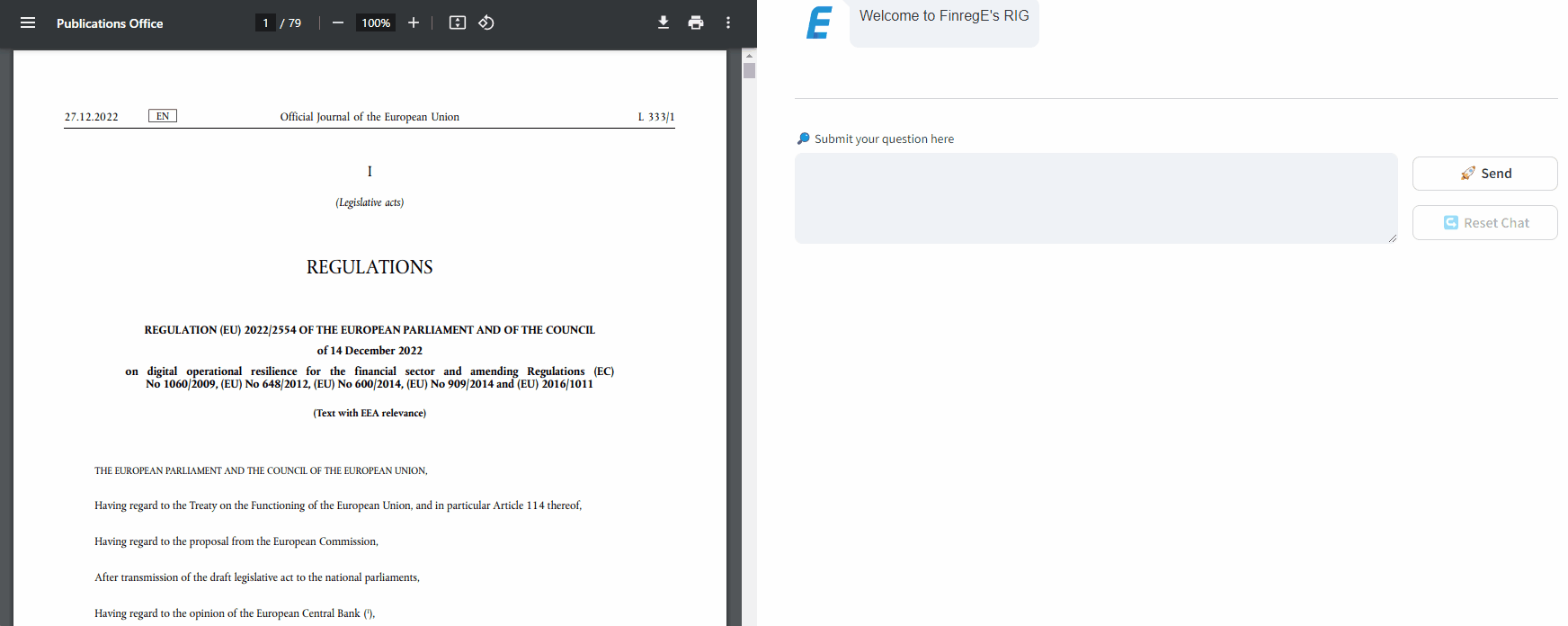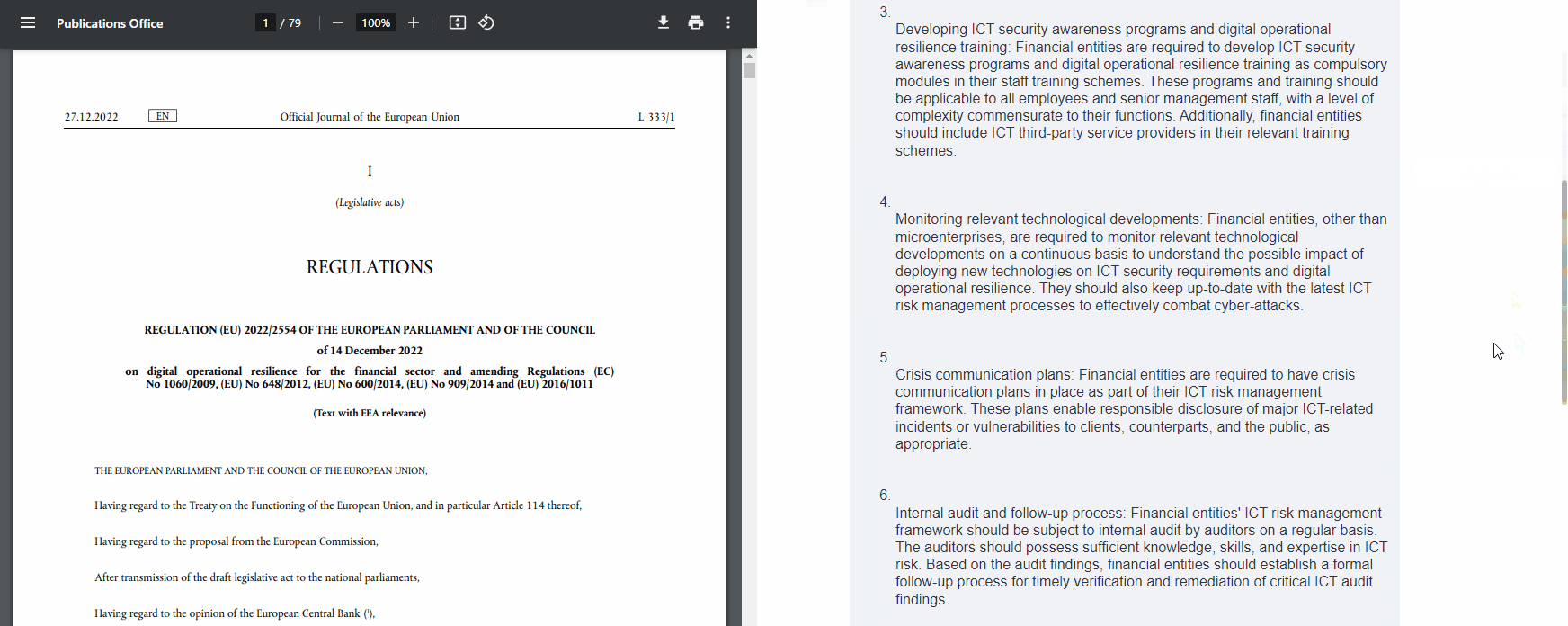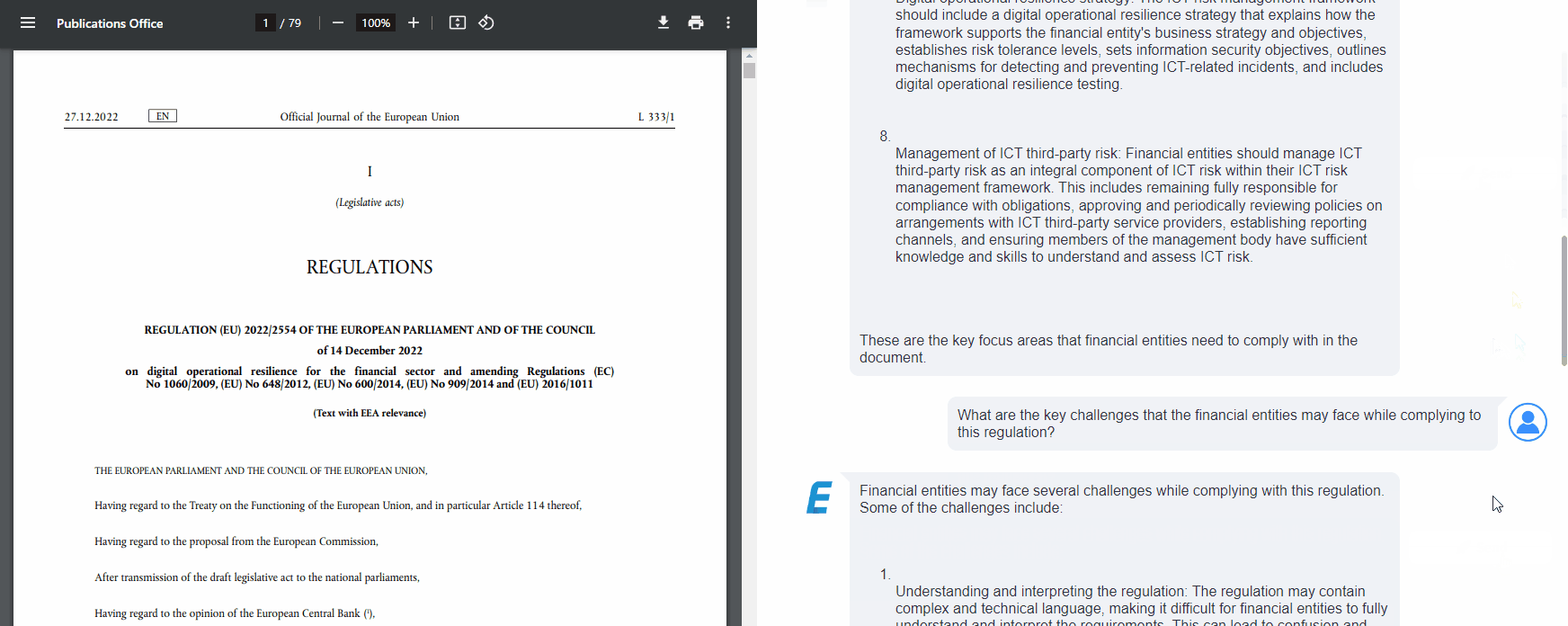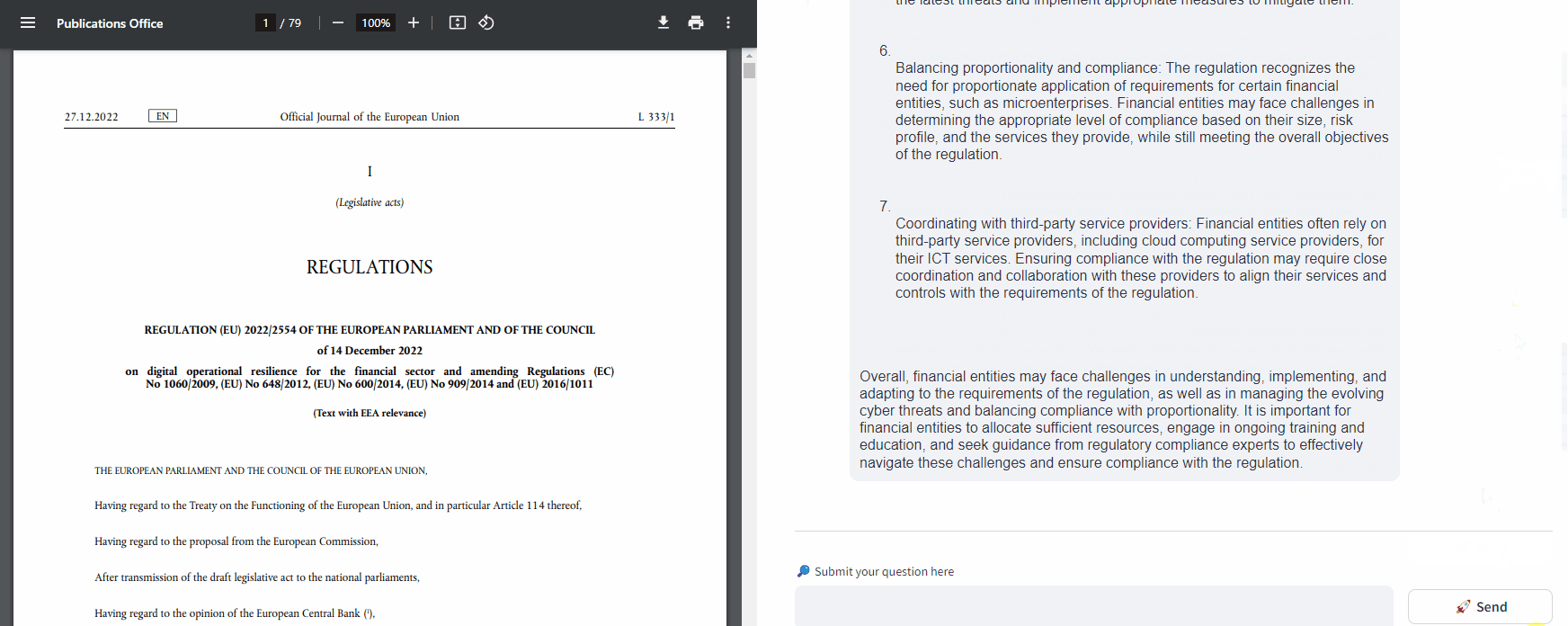
What are the key focus areas that financial entities needs to comply in this document? | The key focus areas that financial entities need to comply with in this document are: · Monitoring the effectiveness of the implementation of their digital operational resilience strategy: Financial entities are required to monitor the effectiveness of their digital operational resilience strategy, including mapping the evolution of ICT risk over time, analysing the frequency, types, magnitude, and evolution of ICT-related incidents, particularly cyber-attacks. This is done to understand the level of ICT risk exposure, especially in relation to critical or important functions, and enhance the cyber maturity and preparedness of the financial entity. · Reporting findings and recommendations: Senior ICT staff are required to report at least yearly to the management body on the findings related to the implementation of the digital operational resilience strategy and put forward recommendations. · Developing ICT security awareness programs and digital operational resilience training: Financial entities are required to develop ICT security awareness programs and digital operational resilience training as compulsory modules in their staff training schemes. These programs and training should be applicable to all employees and senior management staff, with a level of complexity commensurate to their functions. Additionally, financial entities should include ICT third-party service providers in their relevant training schemes. · Monitoring relevant technological developments: Financial entities, other than microenterprises, are required to monitor relevant technological developments on a continuous basis to understand the possible impact of deploying new technologies on ICT security requirements and digital operational resilience. They should also keep up to date with the latest ICT risk management processes to effectively combat cyber-attacks. · Crisis communication plans: Financial entities are required to have crisis communication plans in place as part of their ICT risk management framework. These plans enable responsible disclosure of major ICT-related incidents or vulnerabilities to clients, counterparts, and the public, as appropriate. · Internal audit and follow-up process: Financial entities’ ICT risk management framework should be subject to internal audit by auditors on a regular basis. The auditors should possess sufficient knowledge, skills, and expertise in ICT risk. Based on the audit findings, financial entities should establish a formal follow-up process for timely verification and remediation of critical ICT audit findings. · Digital operational resilience strategy: The ICT risk management framework should include a digital operational resilience strategy that explains how the framework supports the financial entity’s business strategy and objectives, establishes risk tolerance levels, sets information security objectives, outlines ICT reference architecture, and implements digital operational resilience testing. The strategy should also include a communication strategy for disclosing required ICT-related incidents. · Management of ICT third-party risk: Financial entities should manage ICT third-party risk as an integral component of their ICT risk management framework. This includes remaining fully responsible for compliance with obligations, approving and periodically reviewing policies on arrangements with ICT third-party service providers, establishing reporting channels, and monitoring the arrangements and risk exposure related to ICT third-party service providers. These are the key focus areas that financial entities need to comply with in the document. |
What are the key challenges that the financial entities may face while complying to this regulation? | Financial entities may face several challenges while complying with this regulation. Some of the challenges include: 1. Understanding and interpreting the regulation: The regulation may contain complex and technical language, making it difficult for financial entities to fully understand and interpret the requirements. This can lead to confusion and potential misinterpretation of the obligations. 2. Implementing new controls and processes: Financial entities may need to establish new controls, processes, and policies to comply with the regulation. This can be a time-consuming and resource-intensive task, requiring significant planning and coordination across different departments within the organization. 3. Ensuring comprehensive ICT risk management: The regulation emphasizes the need for comprehensive ICT risk management, including incident reporting, testing, and third-party risk management. Financial entities may struggle to develop and implement robust ICT risk management frameworks that cover all necessary aspects and align with the requirements of the regulation. 4. Adapting to increased harmonization and higher standards: The regulation introduces more stringent requirements on ICT risk management compared to existing financial services laws. Financial entities may need to enhance their existing practices and systems to meet these higher standards, which can be challenging and costly. 5. Dealing with the evolving cyber threat landscape: Financial entities need to maintain updated and reliable ICT systems to ensure technological resilience and effectively deal with cyber threats. However, the cyber threat landscape is constantly evolving, and financial entities may struggle to keep pace with the latest threats and implement appropriate measures to mitigate them. 6. Balancing proportionality and compliance: The regulation recognizes the need for proportionate application of requirements for certain financial entities, such as microenterprises. Financial entities may face challenges in determining the appropriate level of compliance based on their size, risk profile, and the services they provide, while still meeting the overall objectives of the regulation. 7. Coordinating with third-party service providers: Financial entities often rely on third-party service providers, including cloud computing service providers, for their ICT services. Ensuring compliance with the regulation may require close coordination and collaboration with these providers to align their services and controls with the requirements of the regulation. Overall, financial entities may face challenges in understanding, implementing, and adapting to the requirements of the regulation, as well as in managing the evolving cyber threats and balancing compliance with proportionality. It is important for financial entities to allocate sufficient resources, engage in ongoing training and education, and seek guidance from regulatory compliance experts to effectively navigate these challenges and ensure compliance with the regulation. |
Suggest a control framework for financial entities based on the requirements of this document? | Based on the requirements mentioned in the document, I would suggest implementing the following control framework for financial entities:
· Implement a comprehensive ICT risk management framework: Financial entities should establish a sound and well-documented ICT risk management framework as part of their overall risk management system. This framework should include strategies, policies, procedures, ICT protocols, and tools necessary to protect information assets and ICT assets. It should enable the financial entity to address ICT risk quickly, efficiently, and comprehensively, ensuring a high level of digital operational resilience. · Establish a strong governance structure: The management body of the financial entity should have full and ultimate responsibility for managing ICT risk. They should actively engage in steering and adapting the ICT risk management framework and the overall digital operational resilience strategy. The management body should also ensure the allocation of sufficient resources and budget to achieve a high level of digital operational resilience. · Maintain a strong relationship with the Union horizontal cybersecurity framework: Financial entities should ensure consistency with the cybersecurity strategies adopted by the Union horizontal cybersecurity framework, as laid out in Directive (EU) 2022/2555. This includes complying with the ICT security and incident notification requirements set out in the framework. · Establish policies for handling ICT-related incidents: Financial entities should have specific mechanisms and policies in place for handling all ICT-related incidents and reporting major ICT-related incidents. These policies should outline the steps to be taken in the event of an incident, including response, recovery, and corrective measures. · Implement controls for ICT third-party service providers: Financial entities should establish arrangements and monitoring mechanisms for ICT third-party service providers, including cloud computing service providers. These controls should ensure that critical ICT third-party service providers are included in the Oversight Framework established by the Regulation. The designation mechanism should consider the dimension and nature of the financial sector’s reliance on such providers. · Provide training and knowledge updates: Members of the management body and staff should receive regular training on ICT risk management. This training should be commensurate with the level of ICT risk being managed and should enable them to understand and assess ICT risk and its impact on the operations of the financial entity. · Proportionate application for certain financial entities: Proportionate application of requirements should be considered for certain financial entities, such as microenterprises and those subject to a simplified ICT risk management framework. Regulatory technical standards developed by the ESAs should not alter the proportionate character of the ICT risk management framework for these entities.
It is important to note that this is a general suggestion based on the information provided in the document. The specific control framework for financial entities may vary depending on the nature, size, and complexity of the institution. It is recommended to consult with legal and compliance experts to tailor the control framework to the specific needs of the financial entity. |
Technical Standards on ICT Related Incidents
Provide a summary of this document in particular technical standards specifying the criteria for the classification of ICT related incidents, materiality thresholds for major incidents and significant cyber threats | The technical standards specified in this document regarding the classification of ICT related incidents, materiality thresholds for major incidents, and significant cyber threats include the following: 1. Classification Criteria: The document specifies the criteria for classifying ICT related incidents and significant cyber threats. This includes criteria such as the amount and number of transactions affected, critical services affected, data losses, reputational impact, duration and service downtime, geographical spread, and economic impact. 2. Materiality Thresholds: The document sets out materiality thresholds for each classification criterion. For example, the materiality threshold for the economic impact criterion is met when the costs and losses incurred by the financial entity from the major incident exceed or are likely to exceed EUR 100,000. Similarly, the materiality threshold for the duration and service downtime criterion is met when the duration of the incident is longer than 24 hours or the service downtime is longer than 2 hours for ICT services that support critical or important functions. 3. Recurring Incidents: The document also addresses recurring incidents, stating that incidents that individually do not constitute a major incident can be considered as one major incident if they meet certain conditions. These conditions include the incidents occurring at least twice within 6 months, having the same apparent root cause, and collectively categorizing as a major incident. 4. Reporting to Competent Authorities: The document outlines the relevance of major incidents to competent authorities in other Member States. It states that the assessment of relevance should be based on whether the incident has a root cause originating from another Member State or whether it has had a significant impact in another Member State. These are some of the technical standards specified in the document regarding the classification of ICT related incidents, materiality thresholds for major incidents, and significant cyber threats. |
What is the list of classification criteria for determining whether an incident constitutes a “major ICT-related incident”? | The classification criteria for determining whether an incident constitutes a “major ICT-related incident” are as follows: 1. Critical services affected: The incident must have had any impact on critical services as referred to in Article 6. 2. Data losses: Any malicious unauthorized access to network and information systems that results in data losses. 3. Clients, financial counterparts, and transactions: The materiality threshold for this criterion can be met if any of the following conditions are met: a) The number of affected clients is higher than 10% of all clients using the affected service. b) The number of affected clients is higher than 100,000 clients using the affected service. c) The number of affected financial counterparts is higher than 30% of all financial counterparts carrying out activities related to the provision of the affected service. d) The number of affected transactions is higher than 10% of the daily average number of transactions carried out by the financial entity related to the affected service. e) The amount of affected transactions is higher than 10% of the daily average value of transactions carried out by the financial entity related to the affected service. f) Any identified impact on clients or financial counterparts that have been identified as relevant as an outcome of the assessment made by the financial entity. 4. Reputational Impact: Any impact on reputation as set out in Article 2. 5. Duration and Service Downtime: The incident duration is longer than 24 hours, or the service downtime is longer than 2 hours for ICT services that support critical or important functions. 6. Geographical Spread: Any impact of the incident identified in the territories of at least two Member States. 7. Economic Impact: Costs and losses incurred by the financial entity exceed or are likely to exceed a certain threshold. It is important to note that for an incident to be classified as a major ICT-related incident, it must meet the mandatory condition of critical services affected, and either one of the data losses criteria or the materiality thresholds of any other two criteria. |
What is mentioned about the criteria and materiality thresholds for determining significant cyber threats in this document? | In this document, the criteria and materiality thresholds for determining significant cyber threats are outlined. The document specifies that for a cyber threat to be considered significant, it must meet the following conditions:
Additionally, the document provides materiality thresholds for different classification criteria:
The document also mentions that recurring incidents that individually do not constitute a major incident can be considered as one major incident if they meet certain conditions, such as occurring at least twice within 6 months and having the same apparent root cause. Overall, the document provides specific criteria and materiality thresholds that financial entities should consider when determining significant cyber threats. |
What is mentioned about addressing recurring incidents and the relevance of major incidents to competent authorities in other Member States? | The document mentions that there were concerns raised about the operational burden and proportionality of analysing recurring incidents, as well as concerns about the assessment of recurring incidents based on common root causes, similar nature, and impact. In response to these concerns, the ESAs have made changes to the provisions related to recurring incidents. They have exempted smaller financial entities from the obligations to report recurring incidents to ensure proportionality. They have also changed the approach for assessing recurring incidents from a rolling basis to a monthly basis to provide timely information without posing a burden to reporting entities. Additionally, the ESAs have focused the common aspects of recurring incidents on the root cause only and deleted references to similar nature and impact. Regarding the relevance of major incidents to competent authorities in other Member States, the document states that the assessment of whether a major incident is relevant to competent authorities in other Member States should be based on whether the incident has a root cause originating from another Member State or whether the incident has or had a significant impact in another Member State. The impact of the incident should be assessed against all Member States, and if there is any impact in at least two Member States, financial entities should consider the criterion being met. The ESAs have made amendments to the draft RTS to reflect this assessment. |
Technical Standards on ICT TPP policy
Provide a summary of this document | The document is a final report on the draft regulatory technical standards for specifying the detailed content of the policy related to contractual arrangements on the use of ICT services supporting critical or important functions provided by ICT third-party service providers. This report is in accordance with Regulation (EU) 2022/2554. The document consists of several sections. 1. Executive Summary: This section provides a brief overview of the report’s contents and key findings. 2. Background and rationale: This section explains the reasons and justifications for the development of the regulatory technical standards. It provides context on the importance of ensuring the security and reliability of ICT services provided by third-party service providers. 3. Draft regulatory technical standards: This section presents the actual draft regulatory technical standards. It specifies the detailed content of the policy, including requirements and guidelines for contractual arrangements with ICT third-party service providers. This section may include clarifications and amendments to previous versions of the standards. 4. Accompanying documents: This section includes additional documents related to the draft regulatory technical standards. · Draft cost-benefit analysis / impact assessment: This document assesses the potential costs and benefits of implementing the regulatory technical standards. It provides an analysis of the economic and practical implications of the standards. · Summary of responses to the consultation: This document summarizes the feedback and comments received during the consultation process for the draft regulatory technical standards. It may include a summary of the main concerns, suggestions, and considerations raised by stakeholders. Overall, the document serves as a comprehensive report on the development and content of the draft regulatory technical standards for ICT third-party service providers. It provides insights into the rationale behind the standards and includes accompanying documents that support the analysis and decision-making process. |
What are the mandatory steps to be followed by financial entities when contracting with an ICT third-party service providers supporting critical or important functions? | When contracting with ICT third-party service providers supporting critical or important functions, financial entities must follow the following mandatory steps: 1. Define Business Needs: The financial entity must define its business needs before entering into contractual arrangements with prospective third-party service providers. This includes identifying the critical or important functions that will be supported by the ICT services. 2. Conduct Risk Assessment: Before entering into a contractual arrangement, a risk assessment must be conducted at the financial entity level. This assessment should also consider any applicable consolidated and sub-consolidated levels. The risk assessment should take into account all relevant requirements under Regulation (EU) 2022/2554 and applicable sectoral legislations and regulations. It should consider the impact of the provision of ICT services on the financial entity, including operational risks, legal risks, ICT risks, reputational risks, risks to the protection of confidential or personal data, risks linked to data availability, risks linked to the location of data processing and storage, and ICT concentration risks. 3. Due Diligence: The financial entity must have a specified process for selecting and assessing prospective ICT third-party service providers. This process should consider factors such as whether the provider is an intragroup ICT service provider, whether they use or intend to use ICT sub-contractors, their location or the location where data is processed or stored, and their adherence to ethical and socially responsible practices. The due diligence process should also assess the effectiveness of the ICT third-party service providers’ risk management framework, including risk mitigation and business continuity measures. 4. Required Level of Assurance: The policy should specify the required level of assurance concerning the effectiveness of the ICT third-party service providers’ risk management framework. This includes assessing the existence of risk mitigation and business continuity measures and ensuring their functioning within the ICT third-party service provider. 5. Documentation and Reporting: The financial entity should document the due diligence process and the results of the assessment. The policy should also specify the reporting requirements, including the receipt of appropriate reports from the ICT third-party service providers on their activities and services provided, performance assessments with key indicators, control indicators, audits, self-certifications, and independent reviews. The financial entity should also be notified of any ICT-related incidents or operational or security payment-related incidents. 6. Compliance Audits: The policy should prescribe that independent reviews and compliance audits with legal and regulatory requirements and policies are performed. These audits should assess the ICT third-party service providers’ compliance with confidentiality, availability, integrity, and authenticity requirements, as well as the financial entity’s relevant policies and procedures. Overall, financial entities must ensure that they have a comprehensive policy in place that covers all these steps and ensures appropriate risk management, control, and documentation throughout the life cycle of contractual arrangements with ICT third-party service providers supporting critical or important functions. |
Navigate the complex world of financial regulations with ease using FinregE’s advanced Horizon scannong software and AI RIG. Book a demo today and streamline your regulatory change management with our cutting-edge technology and ensure your institution stays ahead of regulatory trends and requirements.